Cyber Security
-
Posted: November 23, 2023Read more
Secure the Future: Cisco's Next-Gen Firewall Migration Guide Secure the Future: Cisco's Next-Gen Firewall Migration Guide
Elevate your organization's security in the digital era with Cisco's Next-Generation Firewall (NGFW). Emphasizing the critical need for enhanced network security, the post outlines a structured migration approach, guiding organizations to check their current NGFW model, review migration paths, and collaborate with trusted Security Account Managers or Partners. Explore tailored migration options for Cisco ASA 5500-X Series and boost performance with throughput enhancements for diverse Cisco firewall models. #Cybersecurity #NGFW #NetworkSecurity ????????
-
Posted: November 23, 2023Categories: Cyber SecurityRead more
Expert Evaluation: Next-Gen Firewalls (NGFWs) Explore the dynamic landscape of Next-Generation Firewalls (NGFWs)
Elevate your organization's security in the digital era with Cisco's Next-Generation Firewall (NGFW). Emphasizing the critical need for enhanced network security, the post outlines a structured migration approach, guiding organizations to check their current NGFW model, review migration paths, and collaborate with trusted Security Account Managers or Partners. Explore tailored migration options for Cisco ASA 5500-X Series and boost performance with throughput enhancements for diverse Cisco firewall models. #Cybersecurity #NGFW #NetworkSecurity ????????
-
Posted: October 23, 2023Categories: Cyber SecurityRead more
Ransomware Defense Summary HPE Compute and VMware vSphere collaborate for robust ransomware defense using zero trust and defense-in-depth strategies.
HPE ProLiant Compute establishes a secure edge-to-cloud posture, and VMware provides comprehensive software solutions for intrusion detection, endpoint protection, and data recovery.
This collaboration creates a powerful defense against ransomware threats, detailed in the "Defeating Ransomware" white paper.
-
Posted: July 14, 2022Read more
الفدية Ransomware وسيلة شائعة لمجرمي الإنترنت للاستفادة من أنشطتهم. يستخدمون برامج الفدية لتشفير البيانات الأساسية للشركات ويطلبون دفع فدية في المقابل. إذا لم تقم الشركات بعمل نسخة احتياطية من معلوماتها ، فيجب عليها البحث في جيوبها لاستعادتها.
-
Posted: December 16, 2021Categories: Cyber SecurityRead more
Ransomware is never going to go away in the foreseeable future, but we have to keep working on it," says Edwards. "We can make things better, and that's what we're doing. It may be a cliché, but it really is an arms race
-
Posted: November 19, 2021Categories: Cyber SecurityRead more
Rushing to digital transformation adds risk, but enterprises can mitigate that by bringing security teams on board at the start of every project
-
Posted: November 19, 2021Categories: Cyber SecurityRead more
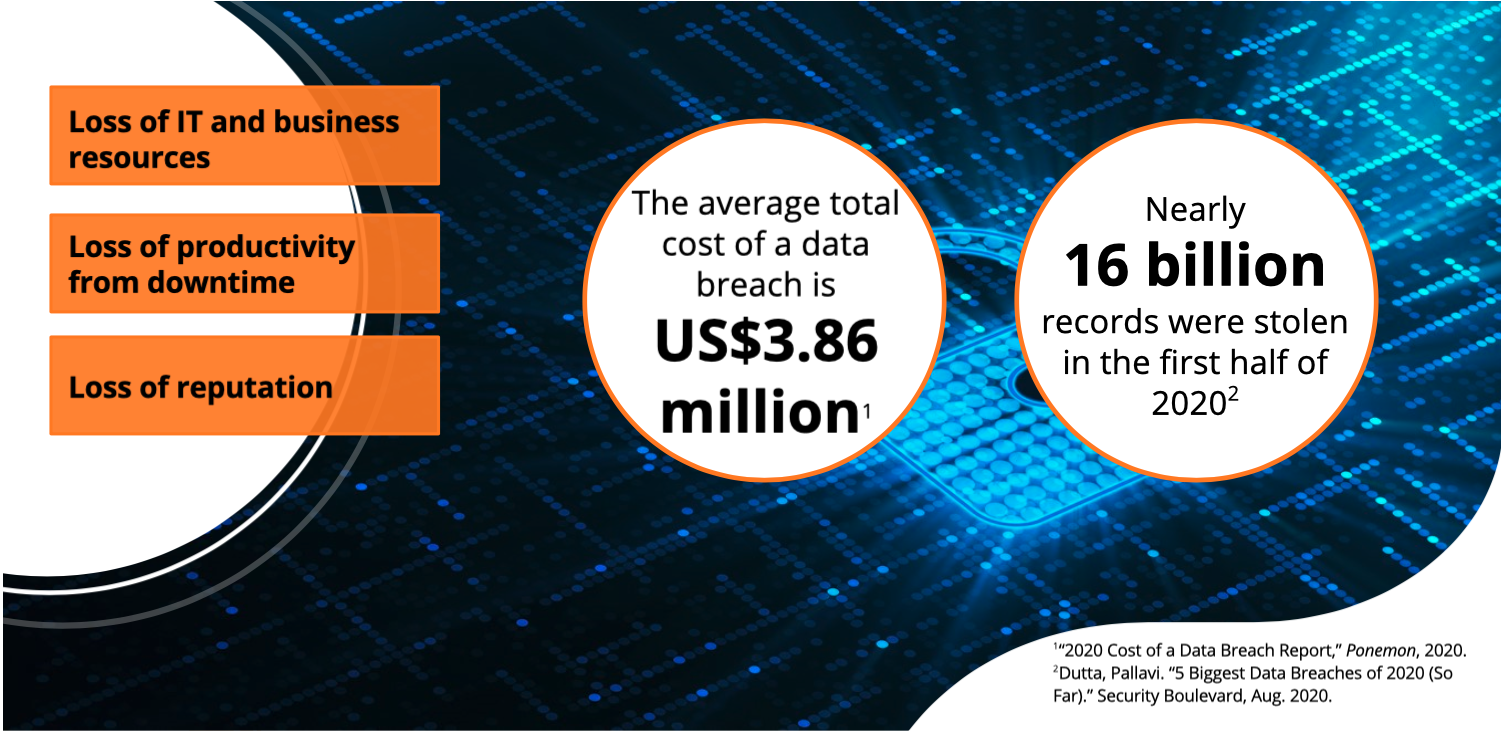
If security is not top of mind for your customers, it should be. Security breaches can be disastrous for IT and for the business as a whole. Victims of ransom ware and other malware attacks may need to pay large sums of cash or spend considerable IT resources to recover and get the network up and running. These breaches can result in a loss of productivity from downtime, and can even stop business. Breaches can also permanently damage the company's reputation and future sales. When personal information is stolen, lawsuits and loss of customers can continue to harm companies long after the breach.
-
Posted: August 09, 2021Categories: Cyber SecurityRead more
As cyber threats become ever more complex, the pressure to have the right endpoint solution in place has also grown. However, the endpoint security marketplace has become congested with many different solutions, and is so full of indefensible marketing claims that making an educated decision for your organization is increasingly difficult. This guide provides clarity by walking you through the key endpoint security technologies to ensure you have the right protection in place. It also enables you to see how different vendors stack up in independent tests, helping you make an informed choice.
The uncomfortable truth about endpoint security
The endpoint security market is full of hype and extravagant claims. However, the reality is that 68% of organizations fell victim to a cyberattack in the last year1. That’s why world-class protection is the foundation of any effective security strategy. However, protection alone is not enough. Four out of five organization admit having a shortage of internal security expertise1. With this in mind usability is also essential if hard-pressed IT teams are to make best use of the protection capabilities. You should also assume that a threat will get through your defenses and equip your organization accordingly. This includes having full visibility into how threats enter the organization, where they went, and what they touched so that you can neutralize the attack and plug any security gaps. Use this guide to understand the protection technologies available and make and informed choice of endpoint protection products.
Product Features and Capabilities
Endpoint security solutions, sometimes referred to simply as antivirus solutions, may include a variety of foundational (traditional) and modern (next-gen) approaches to preventing endpoint threats. W
-
Posted: January 01, 2021Categories: Cyber SecurityRead more
For several years now, HPE has recognized that our world is becoming data-driven, edge-centric, and For several years now, HPE has recognized that our world is becoming data-driven, edge-centric, and cloud-enabled. You will learn more about what this means for you and your customers.”